-
Notifications
You must be signed in to change notification settings - Fork 27
feat: cloudconnector deployment on AppRunner #85
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Merged
Merged
Changes from 34 commits
Commits
Show all changes
36 commits
Select commit
Hold shift + click to select a range
2e38e76
feat: apprunner poc
penguinjournals f5182be
WIP
penguinjournals a0548a0
feat: doc update
penguinjournals d95d779
WIP
penguinjournals 374407d
chore: add name to apprunner service name to privent name colision
hayk99 6e0ae78
Merge branch 'master' into feat-apprunner-poc
penguinjournals 939f247
feat: cloudconnector deploy on apprunner
penguinjournals 0baaeba
Merge branch 'feat-apprunner-poc' of github.com:sysdiglabs/terraform-…
penguinjournals 50ef9e3
fix: changed name for apprunner task to fix aws requirements of length
penguinjournals c3a077d
Merge branch 'master' into feat-apprunner-poc
penguinjournals 96afdd2
fix: task name to avoid confusion
penguinjournals 9a9ac9b
fix: precommit
penguinjournals 2c6b241
retrigger checks
penguinjournals 97a697e
chore: linter fixing
penguinjournals 02135cf
doc: apprunner diagram updated
penguinjournals ff8430a
chore: sequential test
26befc9
chore: sequential test
553099f
chore: sequential test
6a90df8
chorus: timeout increased to pass tests on CI
penguinjournals 1d9be6d
Merge branch 'feat-apprunner-poc' of github.com:sysdiglabs/terraform-…
penguinjournals 0cce02d
chorus: ci test region changed to fit apprunner
penguinjournals 4aef63f
chore: name per test
0873ae8
Merge branch 'feat-apprunner-poc' of github.com:sysdiglabs/terraform-…
0c16f8b
docs: snippet fixed
penguinjournals 58024c3
Merge branch 'feat-apprunner-poc' of github.com:sysdiglabs/terraform-…
penguinjournals ef309b1
chore: fix naming length
1a9c8b0
feat: retrieve cloud connector from new registry
penguinjournals 67a415a
docs: readme updated to explain the apprunner option
penguinjournals 83fd08b
Merge branch 'feat-apprunner-poc' of github.com:sysdiglabs/terraform-…
penguinjournals b16654f
docs: updated broken image links
penguinjournals d347c20
Merge branch 'master' into feat-apprunner-poc
penguinjournals d7dcb1d
docs: fixed typo error
penguinjournals 07bf221
docs: several naming fixes
penguinjournals 5f5146d
feat: versions upgraded
penguinjournals cb28b13
docs: updated url for diagram to fit master
penguinjournals 3278a0c
docs: versions updated
penguinjournals File filter
Filter by extension
Conversations
Failed to load comments.
Loading
Jump to
Jump to file
Failed to load files.
Loading
Diff view
Diff view
There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
|
|
@@ -51,25 +51,37 @@ For other Cloud providers check: [GCP](https://github.com/sysdiglabs/terraform-g | |
| ## Usage | ||
|
|
||
| - There are several ways to deploy this in you AWS infrastructure, gathered under **[`/examples`](./examples)** | ||
| - [Single Account on ECS](#--single-account-on-ecs) | ||
| - [Single Account on AppRunner](#--single-account-on-apprunner) | ||
| - [Single-Account with a pre-existing Kubernetes Cluster](#--single-account-with-a-pre-existing-kubernetes-cluster) | ||
| - [Organizational](#--organizational) | ||
| - Many module,examples and use-cases provide ways to **re-use existing resources (as optionals)** in your infrastructure (cloudtrail, ecs, vpc, k8s cluster,...) | ||
| - Find some real **use-case scenario explanations** under [`/examples-internal/use-cases*`](./examples-internal) | ||
| - [Single Account - Existing Cloudtrail](./examples-internal/use-cases-reuse-resources/single-existing-cloudtrail.md) | ||
| - [Organizational - Existing Cloudtrail, ECS, VPC, Subnet](./examples-internal/use-cases-reuse-resources/org-existing-cloudtrail-ecs-vpc-subnet.md) | ||
| - [Organizational - Existing Cloudtrail withouth SNS, but with S3 configuration, with K8s Cluster and Filtered Cloudtrail Event Account](./examples-internal/use-cases-self-baked/org-s3-k8s-filtered-account.md) | ||
|
|
||
| ### - Single-Account | ||
| ### - Single-Account on ECS | ||
|
|
||
| Sysdig workload will be deployed in the same account where user's resources will be watched.<br/> | ||
| More info in [`./examples/single-account`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account) | ||
| More info in [`./examples/single-account-ecs`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account-ecs) | ||
|
|
||
|  | ||
| 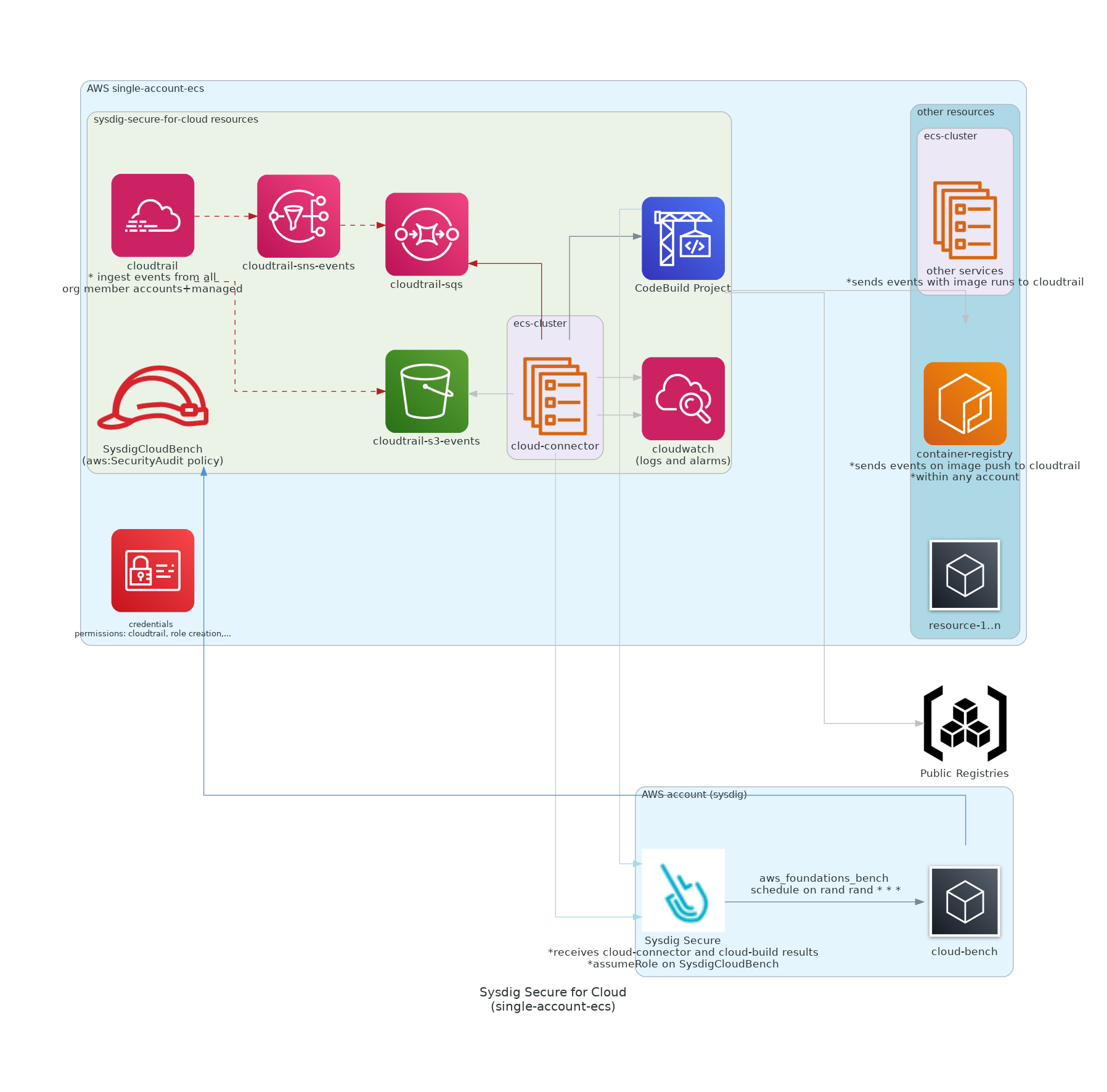 | ||
|
|
||
| ### - Single-Account on AppRunner | ||
|
|
||
| Sysdig workload will be deployed using AppRunner in the same account where user's resources will be watched.<br/> | ||
| More info in [`./examples/single-account-apprunner`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account-apprunner) | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more.
|
||
|
|
||
| 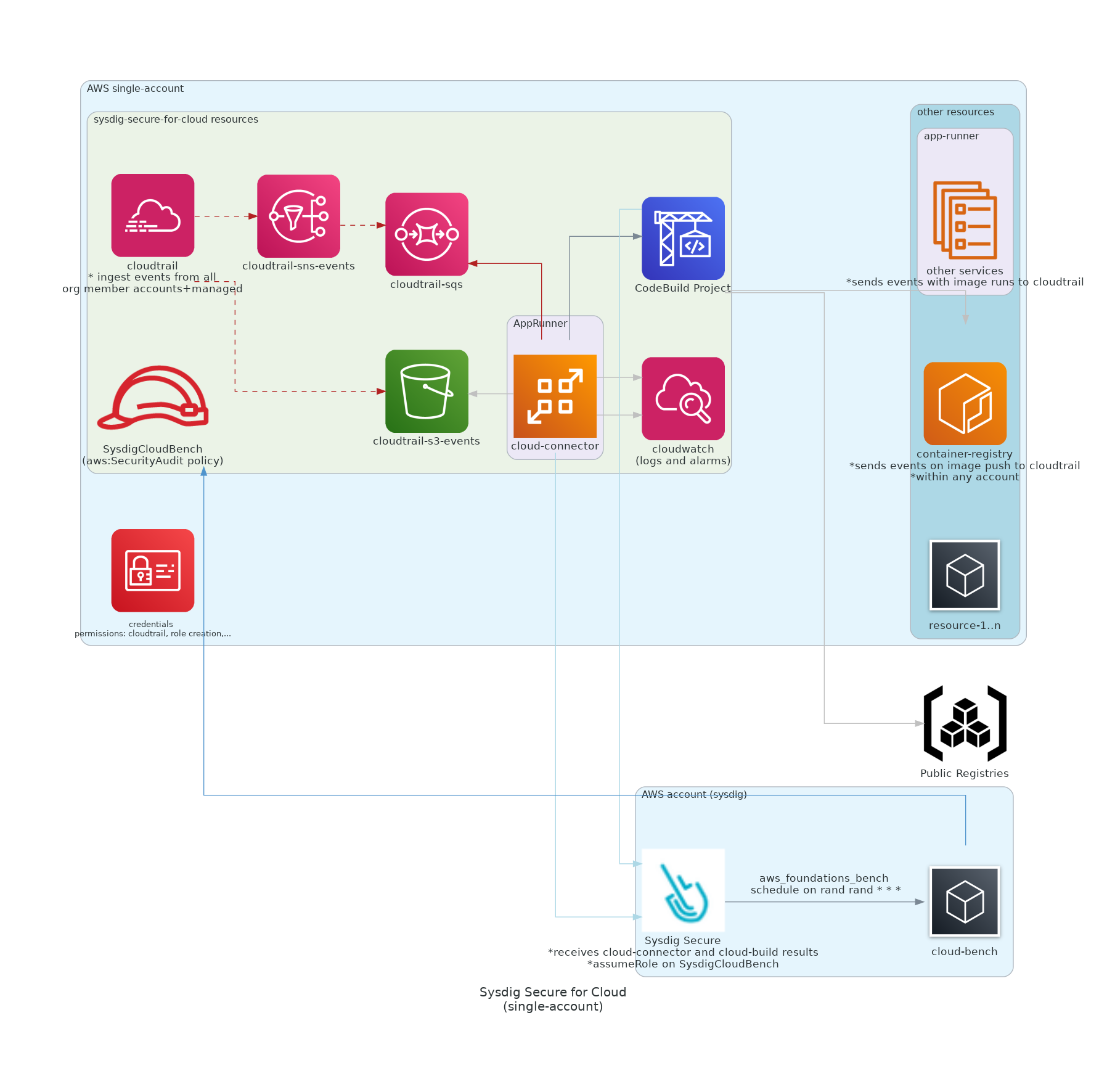 | ||
|
|
||
| ### - Single-Account with a pre-existing Kubernetes Cluster | ||
|
|
||
| If you already own a Kubernetes Cluster on AWS, you can use it to deploy Sysdig Secure for Cloud, instead of default ECS cluster.<br/> | ||
| More info in [`./examples/single-account-k8s`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account-k8s) | ||
|
|
||
|  | ||
|
||
|
|
||
| ### - Organizational | ||
|
|
||
| Using an organizational configuration Cloudtrail.<br/> | ||
|
|
||
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,128 @@ | ||
| # Sysdig Secure for Cloud in AWS<br/>[ Example :: App Runner ] | ||
|
|
||
| Deploy Sysdig Secure for Cloud in a single AWS account using App Runner.<br/> | ||
| All the required resources and workloads will be run under the same account. | ||
|
|
||
| ## Prerequisites | ||
|
|
||
| Minimum requirements: | ||
|
|
||
| 1. Configure [Terraform **AWS** Provider](https://registry.terraform.io/providers/hashicorp/aws/latest/docs) | ||
| 1. Secure requirements, as input variable value | ||
| ``` | ||
| sysdig_secure_api_token=<SECURE_API_TOKEN> | ||
| ``` | ||
| ## Notice | ||
| * **Resource creation inventory** Find all the resources created by Sysdig examples in the resource-group `sysdig-secure-for-cloud` (AWS Resource Group & Tag Editor) <br/><br/> | ||
| * **Deployment cost** This example will create resources that cost money.<br/>Run `terraform destroy` when you don't need them anymore <br/><br/> | ||
| * **AppRunner enabled zones** AppRunner isn't available in all AWS zones, check [AppRunner Service endpoints](https://docs.aws.amazon.com/general/latest/gr/apprunner.html) for enabled zones. | ||
wideawakening marked this conversation as resolved.
Show resolved
Hide resolved
|
||
| ## Usage | ||
| For quick testing, use this snippet on your terraform files | ||
| ```terraform | ||
| terraform { | ||
| required_providers { | ||
| sysdig = { | ||
| source = "sysdiglabs/sysdig" | ||
| version = ">=0.5.33" | ||
| } | ||
| } | ||
| } | ||
| provider "sysdig" { | ||
| sysdig_secure_api_token = "<SYSDIG_SECURE_URL>" | ||
| sysdig_secure_url = "<SYSDIG_SECURE_API_TOKEN" | ||
| } | ||
| provider "aws" { | ||
| region = "<AWS_REGION> Take care of AppRunner available zones: https://docs.aws.amazon.com/general/latest/gr/apprunner.html" | ||
| } | ||
| module "cloudvision_aws_apprunner_single_account" { | ||
| source = "sysdiglabs/secure-for-cloud/aws//examples/single-account-apprunner" | ||
| name = "<APPRUNNER_SERVICE_NAME>" | ||
| } | ||
| ``` | ||
|
|
||
| See [inputs summary](#inputs) or module module [`variables.tf`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/blob/master/examples/single-account/variables.tf) file for more optional configuration. | ||
|
|
||
| To run this example you need have your [aws account profile configured in CLI](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-profiles.html) and to execute: | ||
| ```terraform | ||
| $ terraform init | ||
| $ terraform plan | ||
| $ terraform apply | ||
| ``` | ||
|
|
||
| <!-- BEGIN_TF_DOCS --> | ||
| ## Requirements | ||
|
|
||
| | Name | Version | | ||
| |------|---------| | ||
| | <a name="requirement_terraform"></a> [terraform](#requirement\_terraform) | >= 0.15.0 | | ||
| | <a name="requirement_aws"></a> [aws](#requirement\_aws) | >= 4.0.0 | | ||
| | <a name="requirement_sysdig"></a> [sysdig](#requirement\_sysdig) | >= 0.5.33 | | ||
|
|
||
| ## Providers | ||
|
|
||
| | Name | Version | | ||
| |------|---------| | ||
| | <a name="provider_sysdig"></a> [sysdig](#provider\_sysdig) | >= 0.5.33 | | ||
|
|
||
| ## Modules | ||
|
|
||
| | Name | Source | Version | | ||
| |------|--------|---------| | ||
| | <a name="module_cloud_bench"></a> [cloud\_bench](#module\_cloud\_bench) | ../../modules/services/cloud-bench | n/a | | ||
| | <a name="module_cloud_connector"></a> [cloud\_connector](#module\_cloud\_connector) | ../../modules/services/cloud-connector | n/a | | ||
| | <a name="module_cloudtrail"></a> [cloudtrail](#module\_cloudtrail) | ../../modules/infrastructure/cloudtrail | n/a | | ||
| | <a name="module_codebuild"></a> [codebuild](#module\_codebuild) | ../../modules/infrastructure/codebuild | n/a | | ||
| | <a name="module_ecs_vpc"></a> [ecs\_vpc](#module\_ecs\_vpc) | ../../modules/infrastructure/ecs-vpc | n/a | | ||
| | <a name="module_resource_group"></a> [resource\_group](#module\_resource\_group) | ../../modules/infrastructure/resource-group | n/a | | ||
| | <a name="module_ssm"></a> [ssm](#module\_ssm) | ../../modules/infrastructure/ssm | n/a | | ||
|
|
||
| ## Resources | ||
|
|
||
| | Name | Type | | ||
| |------|------| | ||
| | [sysdig_secure_connection.current](https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs/data-sources/secure_connection) | data source | | ||
|
|
||
| ## Inputs | ||
|
|
||
| | Name | Description | Type | Default | Required | | ||
| |------|-------------|------|---------|:--------:| | ||
| | <a name="input_benchmark_regions"></a> [benchmark\_regions](#input\_benchmark\_regions) | List of regions in which to run the benchmark. If empty, the task will contain all aws regions by default. | `list(string)` | `[]` | no | | ||
| | <a name="input_cloudtrail_is_multi_region_trail"></a> [cloudtrail\_is\_multi\_region\_trail](#input\_cloudtrail\_is\_multi\_region\_trail) | true/false whether cloudtrail will ingest multiregional events | `bool` | `true` | no | | ||
| | <a name="input_cloudtrail_kms_enable"></a> [cloudtrail\_kms\_enable](#input\_cloudtrail\_kms\_enable) | true/false whether cloudtrail delivered events to S3 should persist encrypted | `bool` | `true` | no | | ||
| | <a name="input_cloudtrail_sns_arn"></a> [cloudtrail\_sns\_arn](#input\_cloudtrail\_sns\_arn) | ARN of a pre-existing cloudtrail\_sns. If defaulted, a new cloudtrail will be created | `string` | `"create"` | no | | ||
| | <a name="input_deploy_benchmark"></a> [deploy\_benchmark](#input\_deploy\_benchmark) | Whether to deploy or not the cloud benchmarking | `bool` | `true` | no | | ||
| | <a name="input_deploy_image_scanning_ecr"></a> [deploy\_image\_scanning\_ecr](#input\_deploy\_image\_scanning\_ecr) | true/false whether to deploy the image scanning on ECR pushed images | `bool` | `true` | no | | ||
| | <a name="input_deploy_image_scanning_ecs"></a> [deploy\_image\_scanning\_ecs](#input\_deploy\_image\_scanning\_ecs) | true/false whether to deploy the image scanning on ECS running images | `bool` | `true` | no | | ||
| | <a name="input_ecs_cluster_name"></a> [ecs\_cluster\_name](#input\_ecs\_cluster\_name) | Name of a pre-existing ECS (elastic container service) cluster. If defaulted, a new ECS cluster/VPC/Security Group will be created | `string` | `"create"` | no | | ||
| | <a name="input_ecs_task_cpu"></a> [ecs\_task\_cpu](#input\_ecs\_task\_cpu) | Amount of CPU (in CPU units) to reserve for cloud-connector task | `string` | `"256"` | no | | ||
| | <a name="input_ecs_task_memory"></a> [ecs\_task\_memory](#input\_ecs\_task\_memory) | Amount of memory (in megabytes) to reserve for cloud-connector task | `string` | `"512"` | no | | ||
| | <a name="input_ecs_vpc_id"></a> [ecs\_vpc\_id](#input\_ecs\_vpc\_id) | ID of the VPC where the workload is to be deployed. Defaulted to be created when 'ecs\_cluster\_name' is not provided. | `string` | `"create"` | no | | ||
| | <a name="input_ecs_vpc_region_azs"></a> [ecs\_vpc\_region\_azs](#input\_ecs\_vpc\_region\_azs) | List of Availability Zones for ECS VPC creation. e.g.: ["apne1-az1", "apne1-az2"]. If defaulted, two of the default 'aws\_availability\_zones' datasource will be taken | `list(string)` | `[]` | no | | ||
| | <a name="input_ecs_vpc_subnets_private_ids"></a> [ecs\_vpc\_subnets\_private\_ids](#input\_ecs\_vpc\_subnets\_private\_ids) | List of VPC subnets where workload is to be deployed. Defaulted to be created when 'ecs\_cluster\_name' is not provided. | `list(string)` | `[]` | no | | ||
| | <a name="input_name"></a> [name](#input\_name) | Name to be assigned to all child resources. A suffix may be added internally when required. Use default value unless you need to install multiple instances | `string` | `"sfc"` | no | | ||
| | <a name="input_tags"></a> [tags](#input\_tags) | sysdig secure-for-cloud tags | `map(string)` | <pre>{<br> "product": "sysdig-secure-for-cloud"<br>}</pre> | no | | ||
|
|
||
| ## Outputs | ||
|
|
||
| | Name | Description | | ||
| |------|-------------| | ||
| | <a name="output_cloudtrail_sns_topic_arn"></a> [cloudtrail\_sns\_topic\_arn](#output\_cloudtrail\_sns\_topic\_arn) | ARN of cloudtrail\_sns topic | | ||
| <!-- END_TF_DOCS --> | ||
|
|
||
|
|
||
| ## Authors | ||
|
|
||
| Module is maintained and supported by [Sysdig](https://sysdig.com). | ||
|
|
||
| ## License | ||
|
|
||
| Apache 2 Licensed. See LICENSE for full details. | ||
File renamed without changes.
File renamed without changes.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Oops, something went wrong.
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Uh oh!
There was an error while loading. Please reload this page.