-
Notifications
You must be signed in to change notification settings - Fork 2.4k
Closed
Description
Description:
When using the new AWS_IAM auth type, the InvokeRole is always set to CALLER_CREDENTIALS even when I specify an override. The problem here is that, it forces the caller to have both API Gateway's invoke permission as well as lambda:InvokeFunction permission. This breaks the API abstraction and leaks implementation details (that there's a Lambda behind API Gateway, and the name of the function).
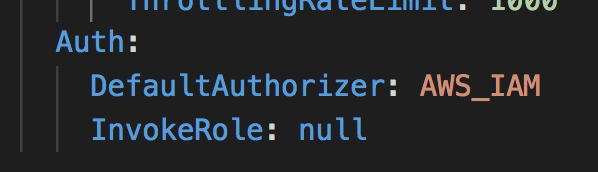
Steps to reproduce the issue:
- create API with auth type set to
AWS_IAMand setInvokeRoletonull
Observed result:
API endpoints still uses CALLER_CREDENTIALS
Expected result:
Execution roleto be `nullInvoke with caller credentialsto bedisabled
tavolate, tommedema, mictian, benkehoe, caspian154 and 8 more